Detecting Firewalls
Jan 16, 2024
As a network based tool, we get a lot of inquiries around connectivity. In fact, I would say the most common problem we have is when users run into firewalls.
What are firewalls?
Are they frustrating pieces of software engineers add to operating systems, servers, subjects, and networking infrastructure to ruin your evening plans and create change event paperwork?
Or are they cutting edge and unstoppable security measures that forever succeed at keeping users and data safe in the internet age?
Well, the answer, as with most things, lies somewhere in the murky middle.
Simply put, firewalls were designed to stop the flow of traffic from one network to another, or from the network to the computer in question. When configured correctly, they work very well, but can make using something like F-Response more difficult.
F-Response depends on the proper flow of traffic over its configured and agree upon ports, as such, if a firewall is blocking that traffic, F-Response is not going to work.
Still, it's not always easy to determine when there is a firewall in place or when you've got some other configuration or networking challenge. As such, when users come to us for help, the first thing we often have them do is run a Wireshark capture of the traffic in question. It's a great way to get a feel for what's going on and helps us look for the best indicator of firewall activity...
The Three Deadly SYNS.
It's not always three, but a little poetic license is allowed.
Basically in a normal TCP session, the initiating party sends a SYN request. The recipient, upon receipt, sends back an ACK response. The initiator then responds with a SYN-ACK.
The entire process is called the "three-part handshake," and looks a little like this:
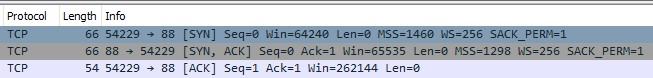
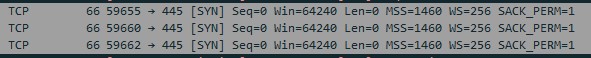
That leaves us with the firewall scenario. The initiating party sends a SYN, then waits, getting no response, it sends a SYN again. Then, with still no response, it sends a third one. This is what I like to call the "Three Deadly SYNS" and you can see it an example of this below.
So, how do you go about figuring this out for yourself? It all starts with a solid network capture. Get yourself a copy of the free network capture tool, Wireshark and follow the steps as outlined in the F-Response Wireshark Support Guide.
Good luck and happy capturing!
Warmest Regards,
M Shannon